Why it’s important
Keeping users signed-in
When transitioning to Rownd’s adaptive authenitcation, it’s often important to keep your existing users signed-in once you deploy Rownd. The token validator enables Rownd to accept and validate your users’ existing tokens. That way, users won’t be forced to sign in again due to the authentication provider upgrade.Moving between apps or contexts
If your app is embedded in one of your customers’ apps, the “parent” app may have previously created its own user session. If the customer can pass you a token or similar data that can be validated either via a JWKset or a REST API, Rownd’s token validator will validate the existing token and extract a user ID from the response so that a user can continue using your app without any friction.How to set it up
To set up the token validator, you’ll need to configure your authentication provider to issue a token that Rownd can validate. Note: If you do not see Integrations in the Rownd left-hand sidebar, please contact the Rownd support team at support@rownd.io for assistance.Configuring the token validator
To set up the token validator with a generic authentication provider, follow these steps:- Navigate to Integrations in the Rownd platform sidebar.
- Enter the API endpoint to be used for token validation.
- Provide information enabling Rownd to extract a user ID
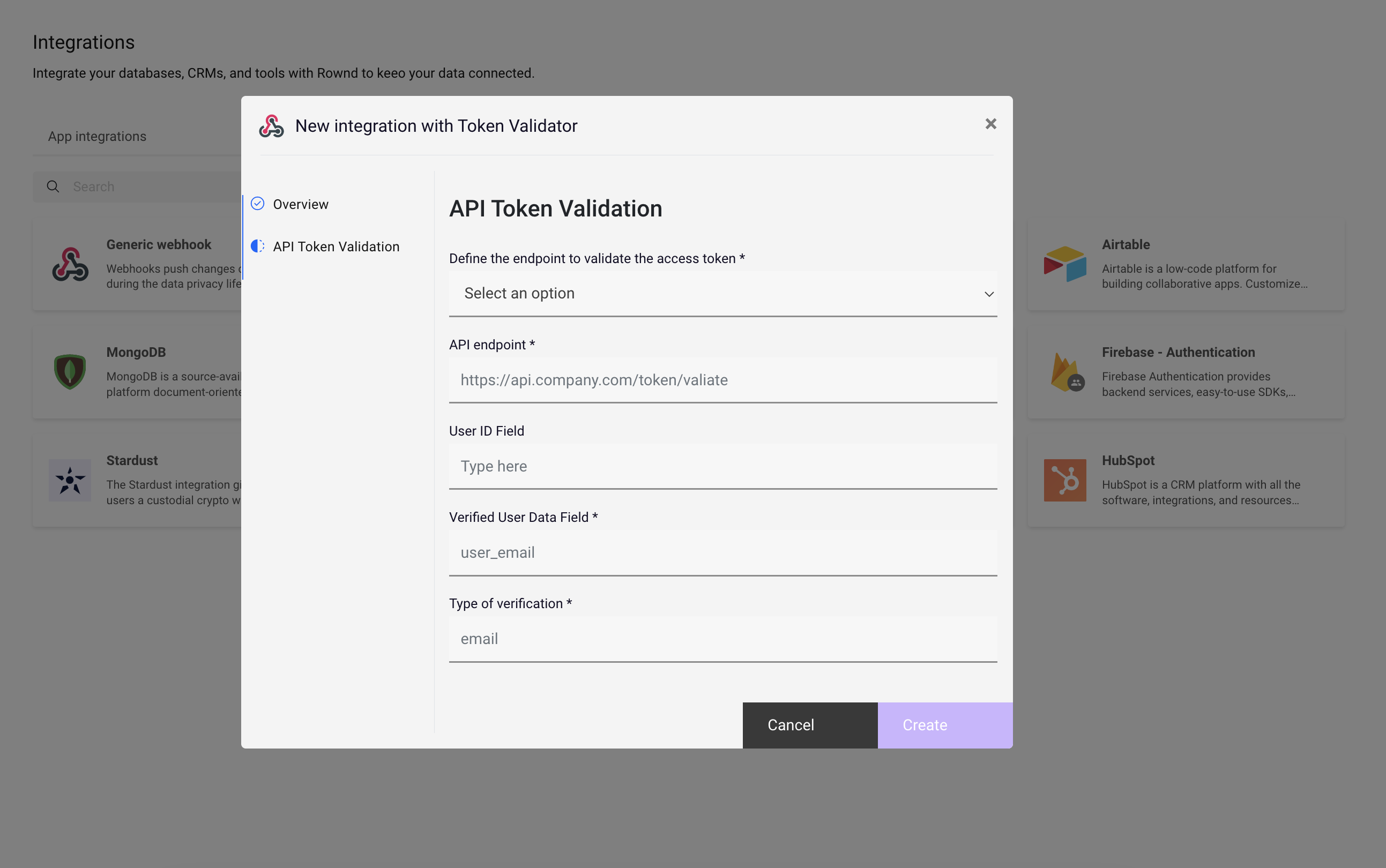
- Attach it to an application
Coming soon:
In the near future, we’ll also support the following configurations:- Adding an OpenID Configuration endpoint or a direct URL to a JWK endpoint that Rownd can use to verify an asymmetrically-signed JWT.
- Adding an HMAC secret that can be used to verify a symmetrically-signed JWT.
Reponding to requests from the token validator
When implementing an API for the token validator to call, the response should be a flat JSON object with properties that match the configuration you supplied to the token validator setup above. For example, if you configured the token validator to extract auserId and email from the response, the response should look like this:
Providing a user ID in your API response is optional. If none is provided, Rownd will generate a new user ID. If the user ID is present, Rownd will use it instead, which may be helpful if you’re trying to map users to an existing system.
Handling cases where the token is invalid or the user isn’t found
If the token Rownd passes to your API does not match an existing user, you should return either a 400 or a 404 status code, which will cause Rownd to abort the token exchange.Firebase setup
If you’re using Firebase as your authentication provider, Rownd provides a separate integration. Follow these steps:- Navigate to Integrations
- Click on the Firebase - Authenticaiton card from the Connector catalog tab.
- Authenticate with Firebase, providing Rownd scoped access for validation.
- Select the desired Project and App (if applicable).
- Save the integration, then attach it to your Rownd application to enable it.